Written By: ThreatInsight Team & Supun Halangoda
Our NodeRisk ThreatInsight Team at NodeRisk was researching Sri Lanka’s exposed vulnerability & threats, with a particular focus on the recent surge in ransomware attacks. This research has uncovered significant security gaps that could potentially expose various sectors to cybercriminal activities. Our findings emphasize the need for a comprehensive cybersecurity strategy that involves:
Over the past few months, our team has been actively researching how ransomware threat actors target Sri Lankan government & organizations. We were able to identify several well-known threat actors, such as LockBit, Alphv, 8base and DarkVault, targeting various entities. There might be more than these, but based on our research, we were able to find the above threat actors, which have already injected ransomware into some entities in Sri Lanka


Published by 8Base

Published by the Play Ransomware Gang

Published by Alphv

Published by LockBit
In recent years, Sri Lanka has witnessed a significant rise in cyber threats, with ransomware attacks becoming increasingly common. These malicious attacks not only disrupt personal and business operations but also pose serious national security threats. To combat this growing menace, it’s crucial to understand the nature of ransomware, its impact, and the measures that can be taken to prevent such cybercrimes.
Understanding Ransomware
Ransomware is a type of malware that encrypts the victim’s data, making it inaccessible, and demands a ransom payment to restore access. The attackers often target businesses, including SMEs, large corporations, and government institutions, exploiting vulnerabilities in their cyber defenses.
What is SMB (Server Message Block)?
SMB stands for Server Message Block. It’s a network communication protocol used primarily for sharing access to files, printers, serial ports, and other resources on a network and this protocol is widely used in many organisations. SMB operates as an application-layer network protocol and utilizes ports 445 also facilitates communication between clients and servers over a network. It enables shared access to files and resources between devices running different operating systems.
This is the same network protocol which was used to spread the “WannaCry Ransomwareˮ which was dependent on NetBIOS and SMB communication ports being left open on hosts and at perimeter firewalls due to misconfigurations on the network of the affected organisations. This port can be actively exploited on vulnerable systems to spread a worm throughout the network, ultimately deploying ransomware on infected machines.
Uncovering Critical Vulnerabilities in Sri Lanka’s Digital Infrastructure Through Open Source Intelligence Investigation
Our Team initiated an Open Source Intelligence OSINT investigation utilizing reputable resources including the widely known search engine “Shodan” and various other sources. Through this investigation, Our Team discovered a concerning vulnerability: over 1000 open SMB ports across our network were found to have Guest logins enabled. This discovery poses a significant risk, as unauthorized access to SMB shares could potentially lead to a catastrophic cyber incident if exploited by threat actors.
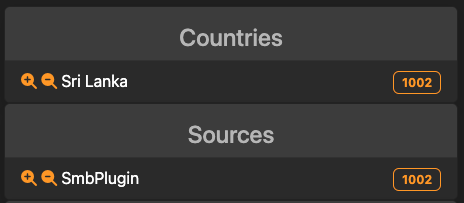
During the analysis of open ports our team discovered an SMB share accessible to the public. Upon further investigation, it was determined that this SMB share had been compromised by ransomware. The entire share, containing critical data such as customer details and financial records, had been encrypted with the “.rpt” file format. This ransomware attack has resulted in the encryption of every file within the SMB share, posing a significant risk to the confidentiality and integrity of sensitive information stored within the affected files.
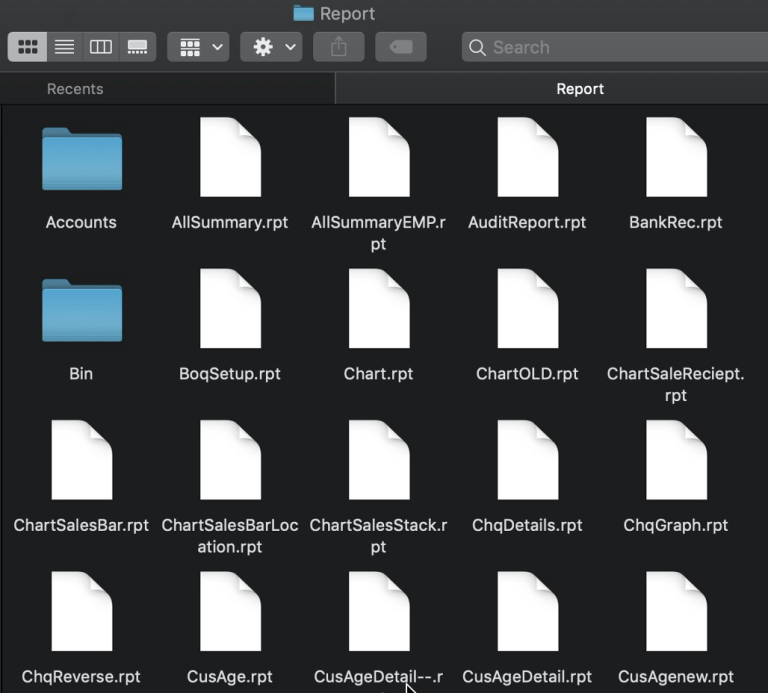
The provided image serves as compelling evidence of a recent ransomware incident within one of Sri Lanka’s reputed organization but the entity has still not uncovered the ransomeware attack. This occurrence underscores the proficiency of threat actors in executing large-scale cyber attacks targeting organizations in Sri Lanka. Such incidents not only highlight the vulnerability of critical systems but also emphasize the urgent need for robust cybersecurity measures to safeguard against potential threats and mitigate the impact of future attacks on essential services and national security.
Additionally, during the system examination, the analyst uncovered a ransomware note deliberately left by the threat actors. This discovery provides further evidence of unauthorized access and malicious intent within the system. Such tactics employed by threat actors underscore the severity of the breach.
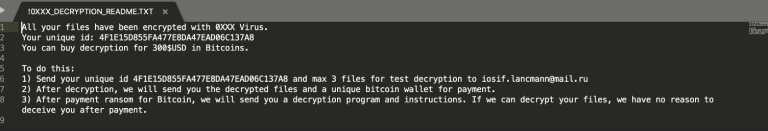
Upon analysis, it has been determined that the SMB share has fallen victim to the “0XXX” ransomware, resulting in the encryption of all files and a ransom demand of $300USD. The examination of relevant details suggests that the threat actors behind this attack originate from Russia, as indicated by the utilization of a mail server based in Russia.
Upon further investigation our team uncover a large POS (Point of Sales) Network where all the POS Machines were open to public internet. These Machines had direct access to there onsite device exposing all users, directories and PII Data. Some of these POS Machines were already infected with ransomeware.
Although these machines had registered users with usernames & passwords. These machines were enabled with “Guest” access mode where anyone could jump into the machine. Our Team suspect that the threat actors used this method to inject the machines through ransomeware.
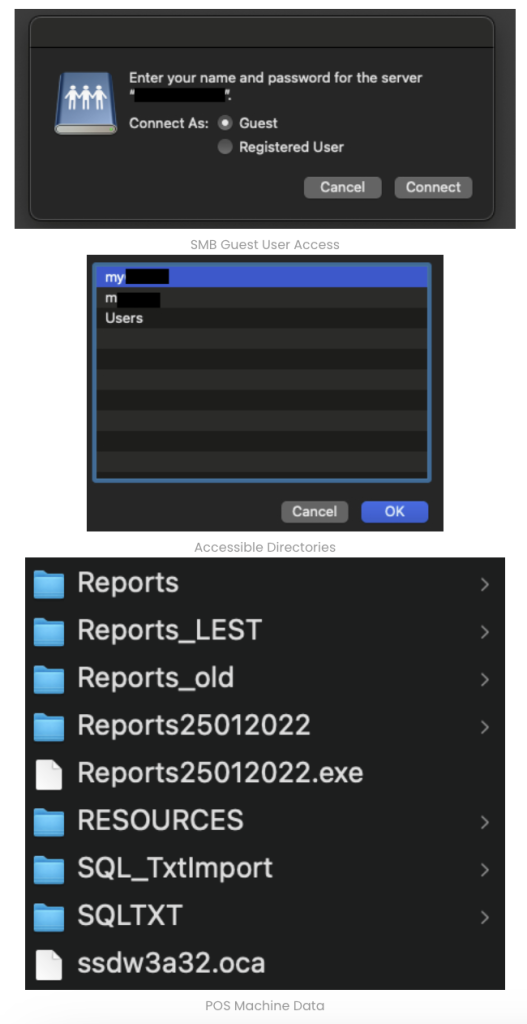
The above evidence illustrates the precise methods by which threat actors can exploit vulnerabilities to plant ransomware within systems. This situation underscores a critical oversight: many organizations in Sri Lanka have not implemented even the minimum cybersecurity measures necessary to defend against such vulnerabilities. This lack of preparedness not only makes it easier for cybercriminals to launch successful attacks but also reflects a broader issue of inadequate cybersecurity prioritization.
Conclusion
In conclusion, while Sri Lanka has made strides in recent years to address cybersecurity challenges, there is still much work to be done. It is imperative for government agencies, private sector entities, and the broader community to collaborate closely, allocate resources effectively, and prioritize cybersecurity initiatives. By fostering a culture of cybersecurity awareness, investing in robust infrastructure, and implementing proactive measures, Sri Lanka can better safeguard its digital assets, protect its citizens, and ensure a secure and resilient cyberspace for all.
Key Areas of Concern:
- Critical Infrastructure: Many of Sri Lanka’s critical infrastructures are increasingly digitized but lack adequate cybersecurity measures, making them prime targets for ransomware attacks.
- Small and Medium Enterprises (SMEs): SMEs often do not have robust security protocols, which leaves them vulnerable to cyber attacks that can cripple their operations.
- Public Awareness: There is a general lack of awareness about cybersecurity practices among the public, which increases the risk of successful phishing and ransomware attacks.
Recommendations for Strengthening Cyber Resilience:
- Government Regulations: Implement stricter cybersecurity regulations and frameworks that all businesses must comply with to protect themselves and their customers.
- Public-Private Partnerships: Encourage collaborations between the government and private sector to share knowledge, resources, and strategies to combat cyber threats.
- Enhanced Security Protocols: Businesses, especially SMEs, should invest in cybersecurity training for their staff and adopt multi-factor authentication, end-to-end encryption, and other advanced security measures.